On 1st of July 2021 we are doing our routine security check on our client website. And as we continue do the full scanning on the site, we found that just like previous post here. We found another php files implanted within a wordpress css core folder at “/wp-admin/css/colors/blue/nys.php”.
According to our experience with wordpress, theres shouldnt be any php files implanted within WordpPress CSS Core files, as such, this is a malicious indicator that something is wrong here.
When we upload the samples to virus total. It confirmed our suspicious when it returned being detected by atleast 11 Security vendor as “Backdoor PHP CN Shell a” by Kaspersky. The VirusTotal link is as per below;
Below is the screenshot of the code contain within the nys.php files.
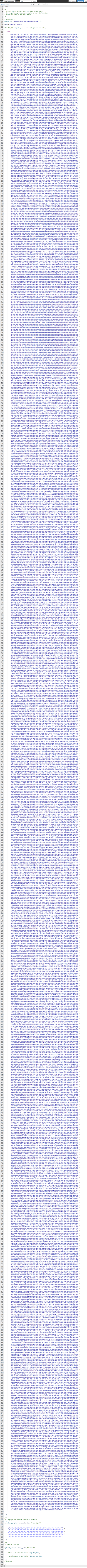
For the time being there’s no indicator that there’s other files might related to this. But it also probably that its part of other leftover malware from the previous hacking towards our customer that you can see here.
We will kept you up to date if we found any new development regarding this.